Link Layer Discovery Protocol (LLDP)
What is the Link Layer Discovery Protocol (LLDP)?
The Link Layer Discovery Protocol (LLDP) is an open and extendable part of the Internet Protocol Suite, commonly known as TCP/IP, used in the IEEE 802.1AB standard to advertise a device's identity and abilities to other connected devices within the same network.
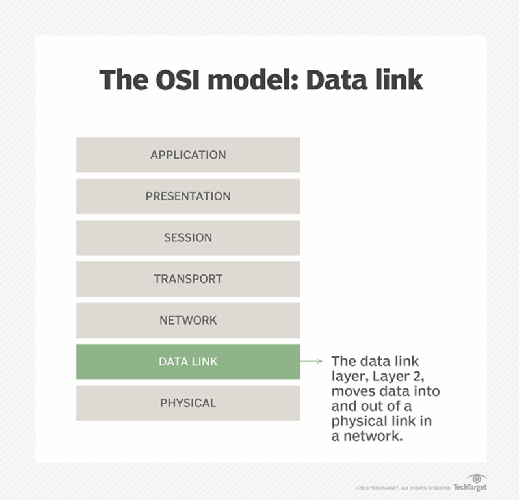
LLDP is an open Neighbor Discovery Protocol that runs over Layer 2, or the data link layer, of the Open Systems Interconnection (OSI) model. In this layer, network monitoring software can discover devices with no recent IP traffic and even devices in a blocked state.
The IEEE 802.1AB standard, from the Institute of Electrical and Electronics Engineers, allows devices to share information to directly connected peers and neighbors. Thus, through LLDP, all devices can send the following information:
- System name and description.
- Chassis identification.
- Port ID.
- Port description.
- Device capability.
- IP address.
- Software version.
- Media access control (MAC) address.
- Medium-dependent interface power.
- Link aggregation.
LLDP is also known as Station and Media Access Control Connectivity Discovery, as specified in IEEE 802.1AB. Similar proprietary protocols include Cisco Discovery Protocol (CDP), Extreme Discovery Protocol, Foundry Discovery Protocol, Microsoft's Link Layer Topology Discovery and Nortel Discovery Protocol.
Where is LLDP used?
LLDP is mainly used in wired Ethernet-connected devices to facilitate the management of network resources and simplify networking tasks for administrators in a multivendor network. One common application of LLDP is data center bridging.
LLDP is also used to advertise Power over Ethernet. PoE refers to the delivery of direct current power to devices over copper Ethernet cabling. It eliminates the need for separate power supplies and outlets, thereby reducing cost, simplifying installation, saving time and improving safety.
Security is another application of LLDP. The advertising of device information through LLDP enables network administrators to identify unauthorized or rogue devices on the network. They can then quarantine or block those devices to prevent security incidents.
LLDP information provides a better understanding of network topology and device capabilities. This network documentation enables admins to plan, upgrade and maintain the network.
How does LLDP work?
To share information with neighboring devices, the LLDP-enabled devices must have an LLDP agent installed. The agent sends advertisements from the device to all physical interfaces. The advertisements can be sent periodically or as changes occur.
LLDP uses three attributes to discover neighbor devices:
- Type (T).
- Length (L).
- Value descriptions (V).
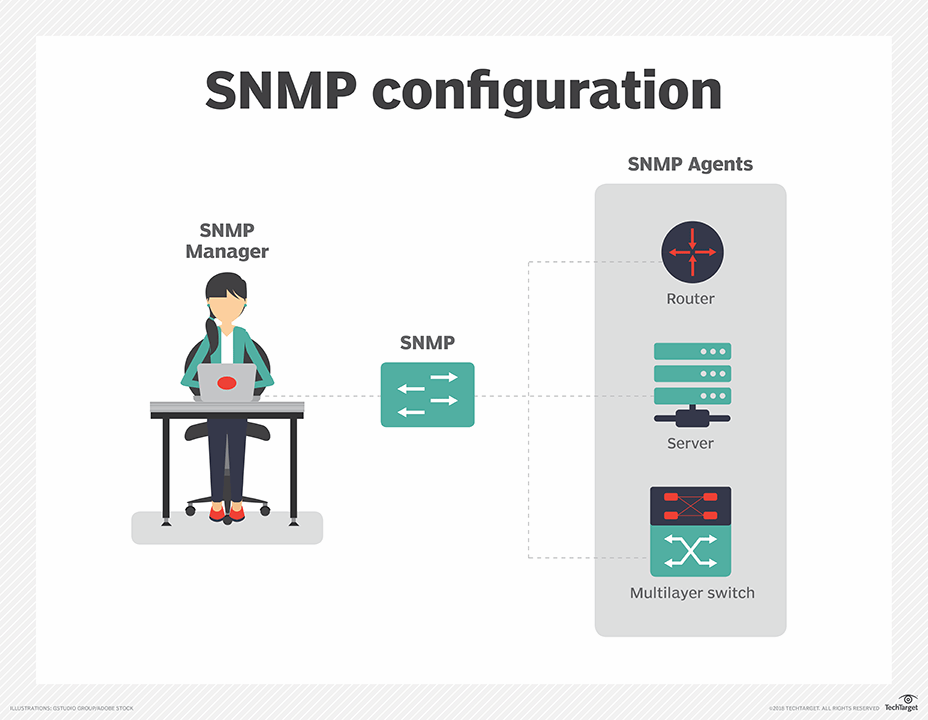
This information is stored in local management information databases (MIBs) and can be queried on demand with Simple Network Management Protocol (SNMP). On an interval schedule, an LLDP device sends its information in Ethernet frames. A frame starts with three required TLVs: chassis ID, port ID and time-to-live. The frame contains the device's destination MAC address as a multicast address that is not forwarded outside a network, assuming IEEE 802.1D compliance.
To retrieve a neighbor's information, network monitoring software uses SNMP queries to scan a device's MIB. The software builds a detailed topology map using its built-in Layer 2 and 3 network discovery and mapping capabilities, using LLDP with Address Resolution Protocol cache discovery. It trawls the network to identify all interconnected devices and build the topology map.
Advantages of LLDP
LLDP's multivendor support enables network discovery of devices and management tools such as SNMP in a network made up of devices from different manufacturers. This capability can help with network troubleshooting and inventory management.
Other benefits of the dynamic discovery of neighboring devices include the following:
- Facilitates the efficient use of network resources.
- Enables admins to optimize network topology.
- Makes it easier to configure devices.
As an open and interoperable protocol, LLDP is supported by multiple networking vendors and can be used with many devices.
Also, LLDP packets -- sent in the form of Ethernet frames, with each frame containing an LLDP data unit -- are small. As a result, when device information is being advertised, it rarely causes network congestion.
Drawbacks of LLDP
Despite LLDP being open and interoperable, not all devices support it for network or device discovery. Some device vendors also implement it differently, creating interoperability issues. Also, the protocol might not be backward compatible with legacy devices or systems. These issues can create challenges for network admins during implementation or troubleshooting, if they prefer to work with LLDP or if the network contains both new and old LLDP-compatible devices.
Another drawback of LLDP is its implementation cost. Compared with other discovery protocols such as CDP, implementing LLDP can require more resources and more time-consuming configurations.
The information provided by LLDP is often sufficient for troubleshooting, network optimization and maintenance, for example. However, for quality of service, traffic shaping, network policy enforcement and other complex applications, LLDP's basic information might not be sufficient. This can be particularly problematic in large or complex networks.
Furthermore, this same basic information can expose the network to cyberattacks. Potential threat actors who eavesdrop on this information could exploit it to gather further intelligence about the network or plan attacks on it.
Common network protocols and their functions are key for communication and connection across the internet. Learn all about common network protocols.
