The big picture: The domain name lookup process is one of the most significant holes in network security. Despite being crucial for translating human-friendly web addresses into IP numbers that computers can understand, DNS is too "open." Everything from your browser to apps to operating system components broadcast DNS requests in the clear, making them vulnerable to snooping and hijacking attacks.

Microsoft is finally doing something about this DNS vulnerability. The company recently released a preview of its new "Zero Trust DNS" (ZTDNS) framework to secure Windows DNS traffic. From what we have seen, it's a pretty comprehensive security overhaul.
The core concept behind ZTDNS is just as it sounds – never automatically trust any domain resolution request until it's thoroughly validated. Under this model, Windows PCs configured for Zero Trust DNS will flatly refuse to connect to any server unless its domain name is explicitly approved and its DNS lookup encrypted and authenticated.
"[Zero Trust DNS] renders the use of hard-coded IP addresses or unapproved encrypted DNS servers irrelevant without having to introduce TLS termination and miss out on the security benefits of end-to-end encryption.," Microsoft explains.
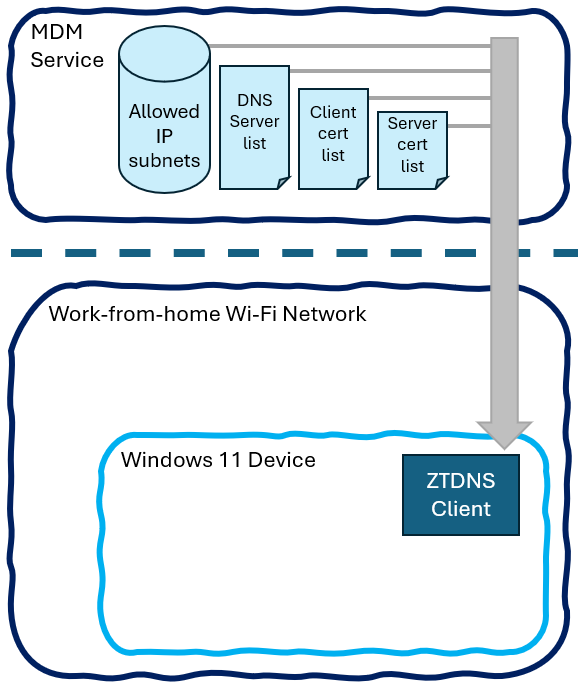
Zero Trust DNS utilizes two existing Windows technologies – the DNS client for handling lookups and the Windows Filtering Platform for enforcing network policies. When enabled, ZTDNS blocks all outbound IPv4 and IPv6 traffic by default, except for approved DNS servers and the bare minimum needed for network discovery. So, any DNS response containing an IP address unlocks an exception for that destination, allowing the corresponding app or service to connect. In contrast, attempts to access an unapproved IP get stonewalled instantly.
Microsoft hopes that widespread Zero Trust DNS adoption helps to block potentially malicious traffic using unverified domain names. The framework could eliminate entire categories of DNS-based attacks and data leaks for businesses and high-risk environments.
Of course, the feature is still in the early preview stage, with no firm timeline for a stable release. However, Microsoft has committed to flighting it to Windows Insiders soon for broader testing.
Microsoft is undergoing a protection overhaul after the US Cyber Safety Review Board criticized past security practices as "inadequate." The Board's concerns arose after major incidents like the Exchange Online hack. The review prompted CEO Satya Nadella to take action. Earlier this week, he dispatched a company-wide memo instructing employees to prioritize security over everything else.
Microsoft's renewed focus explains the unveiling of the ZTDNS framework, potentially one of the first changes corresponding to the shakeup.
Microsoft's 'Zero Trust DNS' could finally rid Windows of widespread DNS vulnerabilities