Palo Alto Networks: Driven By Distribution

Summary
- Palo Alto's strong growth is being driven by its distribution capabilities and a lack of exposure to SMBs.
- While the product business has been performing well, it is likely to become a growth headwind going forward.
- Palo Alto's premium valuation may be due to investors viewing the stock as a good way to gain cybersecurity exposure with less downside risk.

Just_Super
Palo Alto Networks (NASDAQ:PANW) has established itself as a leader in cybersecurity, on the back of a broad portfolio of solutions and a large salesforce. Within SASE and XDR, Palo Alto’s competitive positioning is unclear, but this is unlikely to matter in the short-term. End-market growth, a large firewall customer base and limited exposure to SMBs should support Palo Alto’s growth. While Palo Alto’s valuation looks expensive relative to peers, this premium is likely the result of investors viewing Palo Alto as a relatively low-risk way to gain cybersecurity exposure, on account of its size, stable growth and profitability.
The Cybersecurity Market
Cybersecurity has not been immune to the tech growth slowdown, but is better positioned than most segments due to the critical nature of security. Digital transformation initiatives are ongoing and cyberattacks, like ransomware, continue to be a problem. Palo Alto’s management has suggested that it hasn’t seen a large slowdown, although business leaders are being more cautious due to macro uncertainty, which is leading to increased deal scrutiny. There has been increased pricing pressure and longer deal cycles, but no real reduction in demand. There are also more conversations around payment terms, discounts and deal scope with purchasing teams. This commentary is far more negative than many of Palo Alto’s peers, which could be due to its exposure to hardware or its large deal sizes.
The hardware market is beginning to normalize, backlogs are unwinding and supply chain pressures are easing, and as a result Palo Alto expects lead times to shorten over the next 3-6 months. In addition, hardware budgets could be pressured going forward if customers are reluctant to commit to CapEx in a weak macro environment. Although, Palo Alto sees this as a tailwind for its software firewall business.
Longer-term, Palo Alto is likely to see robust growth across end-markets, particularly cloud security. Around 5-7% of overall IT spend is typically spent on security, but only 1-2% of public cloud spend is currently dedicated to security. Palo Alto believes that public cloud security spend can probably reach around 2.5-3.5% of IT spend, as the cloud hyperscalers already provide infrastructure security. Even with their current high level of success, Palo Alto’s management believes they only have roughly a 3.5% share of a 200 billion USD cybersecurity market.
The cybersecurity market will also continue to expand in response to evolving threats. For example, Palo Alto is currently researching the ability of ChatGPT to generate malware and the ability of its platform to defend against that malware. This is a rapidly developing area where the short-term impact is likely being overstated, but the long-term impact could be large. LLMs like ChatGPT are better suited to simple tasks than complex ones. As a result, they can improve the productivity of more sophisticated cybercriminals or provide less technical cybercriminals with basic capabilities. This could increase the volume of cyberattacks, without necessarily resulting in novel attacks. The ability of LLMs to create plausible sounding text could also be utilized to create phishing emails. Organizations like OpenAI are trying to put controls in place to prevent the abuse of LLMs, but users are likely to find workarounds. There is already an abundance of existing malware that can be used to exploit known vulnerabilities, making ChatGPT just one of many threats that security software must address.
Palo Alto Networks
Palo Alto Networks offers customers the broadest portfolio of security solutions in the industry, and is trying to add value by enabling vendor consolidation and improved security through integrated tools and data. Most enterprises have around 30 to 40 security vendors, and data must be collected from these vendors before it can be analyzed. Platform consolidation simplifies ensuring data quality and analyzing security data across an organization.
Palo Alto has largely built its portfolio through acquisitions, which aligns with the current CEO’s experience as a former president at SoftBank and as an advisor to a private equity firm. While acquisitions and a large distribution footprint have allowed Palo Alto to rapidly expand, it is still unclear whether the company can successfully integrate all of its solutions into a cohesive package. Pros and cons can be made regarding the technical aspects of Palo Alto’s products relative to peers, but it often appears that the fastest to market approach has been the one chosen, which probably doesn’t bode well for the long-term competitive positioning of the platform.
This is unlikely to matter in the near-term though, as Palo Alto has an extremely large firewall customer base that they can sell next-gen solutions to. Cloud, network, application and endpoint security are large opportunities for Palo Alto, and adjacent markets like identity authorization and permissions could be areas for future expansion.
SASE
Functionally, the five main pillars of SASE are SD-WAN, Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA). SASE vendors manage their customers’ traffic the moment it leaves the endpoint, and as a result the network must be resilient, with low latency and high availability. Vendors can provide this infrastructure themselves or partner with an ISP/hyperscaler and utilize their infrastructure. Cloudflare (NET) maintains its own infrastructure, which provides a cost advantage and can help to differentiate the product. Zscaler (ZS) maintains its own infrastructure and partners with ISPs and cloud providers.
Palo Alto does not have its own network, instead choosing to rely on the hyperscalers (primarily Google Cloud (GOOG)). The stated reason for this being that it is difficult and expensive to build and maintain a network, and that the hyperscalers can provide greater reliability. It is more expensive to rely on the hyperscalers, but Palo Alto’s management has stated that the reliability makes it worthwhile. This is questionable though. Palo Alto was a late entrant to the market and it is possible that the market would have been lost by the time Palo Alto built its own network. Utilizing the hyperscalers may have been a business decision to gain market share in the short-term, rather than a technical decision to implement the best solution. Palo Alto’s advantage in SASE is likely to come from its strong understanding of virtual firewalls and SD-WAN for protecting traffic.
The implementation of SASE is a strategic decision made at the C-suite level, meaning that vendors must have a strong top-down sales motion and engender customer trust. Customers also rely heavily on partners to implement solutions. For example, 93% of Zscaler’s revenue comes through channel partners (resellers and integrators).
The shift from on-prem firewalls to SASE will expand Palo Alto’s market, as SASE deals are generally worth 2.5-3 times more than an equivalent firewall deal. Palo Alto’s SASE business grew close to 80% YoY in the most recent quarter and management believes their SASE business is about one-third the size of the market leader (presumably Zscaler). While these figures are impressive, it needs to be kept in mind that Palo Alto has a large salesforce that is selling into a large existing customer base.

Figure 1: Prisma SASE (source: Palo Alto Networks)
Prisma Cloud
Prisma Cloud is a growth area for Palo Alto, and may be one of its best positioned solutions from a competition perspective. Cloud security is a relatively new segment, which is developing rapidly and does not have dominant vendors like the SASE and endpoint markets. Cloud security involves a broad range of solutions covering elements of application development, run-time protection, identity, access and compliance. Cloud security segments include:
- Cloud Security Posture Management (CSPM) - solutions aim to identify misconfigurations
- Cloud Infrastructure Entitlement Management (CIEMs) - provide infrastructure entitlement management
- Cloud Workload Protection Platforms (CWPPs) - secure cloud workloads
- Cloud-Native Application Protection Platform (CNAPP) - aim to address workload and configuration security by scanning them during development and protecting them at runtime. Encompasses CSPM, CWPP and CIEM.
There is also a convergence occurring between application development, IT operations and security (DevSecOps). Developer platforms are building out security capabilities and security platforms are shifting left into application development workflows. Application development security includes:
- Static application security testing looks at an application’s code.
- Dynamic application security testing checks for vulnerabilities during run-time.
- Manual penetration testing simulates an attack against a running application.
- Software composition analysis looks for vulnerabilities in open-source components.
- Fuzz testing - injects invalid or unexpected inputs into an application to potentially reveal vulnerabilities.
- Container scanning
- Dependency scanning
Palo Alto primarily built its cloud platform through acquisitions:
- Twistlock – container runtime security
- PureSec – security for serverless functions
- Aporeto – workload identity
- Developer security – Bridgecrew, Cider Security
An agent-based approach is used to monitor and control endpoints by using an agent on the endpoint to collect data and enforce security rules. Administering those endpoints can be time consuming and agents consume resources on the endpoint. Agentless solutions monitor from the outside by looking at network and configuration data. Agentless is more of a reporting and compliance tool though as it provides less control. The shift towards microservices in the cloud has created dynamic and ephemeral environments which are difficult to protect with an agent-based approach. Palo Alto primarily uses an agent-based approach for cloud security and may choose to acquire or develop an agentless solution in the future.
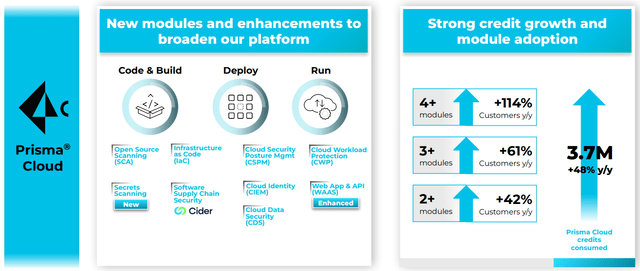
Figure 2: Prisma Cloud (source: Palo Alto Networks)
Cloud security can be approached from an endpoint (CrowdStrike (CRWD)), network (Zscaler) or developer security (GitLab (GTLB)) perspective. This could cause fierce competition, with vendors approaching the market as part of a broader platform strategy.
Cortex
Palo Alto believes that current security operations center approaches are outdated. SIEM is used post-breach or post-event to figure out what happened, and needs enforcement and remediation capabilities and AI to reduce the burden on the security team. Automating the security operations center is important, as there is a labor shortage within cybersecurity. The ultimate goal would be a completely autonomous SOC.
Palo Alto’s capabilities in automation, analytics and attack surface management are allowing it to drive an AI-based SoC transformation. Internally, Palo Alto used to have 67,000 alerts across 200 vendors, creating significant complexity and workload for security operations. This has been replaced with one endpoint agent, a datalake and AI, allowing mean response times to decline from 27 days to under one minute. This approach is now being offered to Palo Alto’s customers through XSIAM.
XSIAM was made generally available in Q1, and so far Palo Alto has closed approximately 30 million USD in business and has a growing pipeline of opportunities. While this is rapid growth, it is tempered by the fact that XSIAM deals are extremely large on average, and hence this likely represents only a handful of deals. Palo Alto expects consolidation within the EDR/XDR space over time, possibly to only three vendors.
85% of an organization’s security data is generated between the endpoint and the firewall, making access to these critical for a data driven approach to security. Palo Alto has 61,000 firewall customers and 4,500 endpoint customers, with a large amount of overlap between the two customer groups.
Modern cybersecurity is largely a data problem, and as a result, SIEMs are being replaced by security data lakes, with the data lake providing a repository for all relevant data. Due to the quantity of data involved, searches can be time consuming and expensive. Cybersecurity data is also often unstructured which complicates search and analysis at scale.
Snowflake (SNOW) is a player in this area due to its ability to combine security feeds with data from the rest of the business, providing greater context. Snowflake's ability to decouple storage from compute is also important due to the volumes involved. A lot of historical data is stored, but generally not all of this data needs to be accessed at the same time. AWS, Azure, and GCP have also launched their own security data lakes, augmented with security integrations.
Again, this is an area where there hasn’t been much technical innovation by Palo Alto. XSIAM uses Google’s Big Query as a datalake, and it has been suggested that XSIAM is extremely expensive. Snowflake has stated that Google’s BigQuery is probably the closest competitor, although Google has lost engineering talent to Firebolt. BigQuery, Redshift and Synapse were not initially built for the cloud, which may be a limiting factor.
XDR platforms may take a closed, open or hybrid approach. Palo Alto is taking a closed approach, attempting to provide the EDR capabilities and all other detection services used to provide context. Open XDR attempts to use the XDR platform as a common layer across existing security tools. CrowdStrike and SentinelOne (S) are taking a hybrid approach where they provide EDR capabilities and some detection services, but also support a tightly integrated ecosystem of partners. Being able to correlate across a large number of disparate data sources is what makes a strong security program, potentially providing open platforms with an advantage.
CrowdStrike and SentinelOne are both taking an indexless approach to managing security data. With index-free logging, data is stored in buckets, which are labeled with information that enables the query engine to decide if data should be included or not. Indexless approaches eliminate data schema requirements from the ingestion process and index limitations from querying. This is beneficial for unstructured data and enables faster results at a fraction of the cost compared to traditional approaches. Indexes are better suited to systems with low ingest rates and high query frequency. This is the opposite of logging though, where ingest rates are high and query frequencies low. Index-free logging reduces ingest latency, provides near real-time alerts and lowers disk space requirements.
Financial Analysis
Growth remains fairly robust across both the product and software businesses, despite macro headwinds. Palo Alto sees no reason why revenue can’t double again, given robust end-market growth and expansion of its solutions.
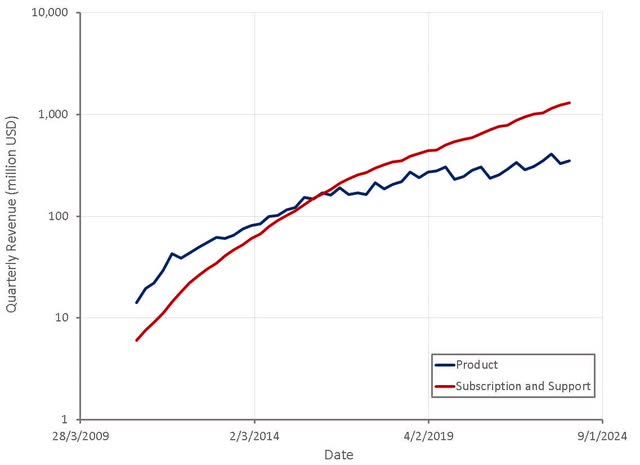
Figure 3: Palo Alto Revenue (source: Created by author using data from Palo Alto Networks)
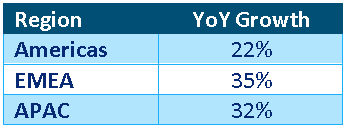
Table 1: Palo Alto Second Quarter FY2023 Growth by Region (source: Created by author using data from Palo Alto)
Management expects growth to remain robust through the remainder of FY2024, and this lack of deceleration is likely what has driven the share price in recent months. Palo Alto's growth will decelerate going forward though, which will make the current stock price look expensive.
With a normalization of the hardware side of the business and the acquisition related growth spurt dying down, it would not be surprising to see Palo Alto’s growth settle below 20% in coming years.
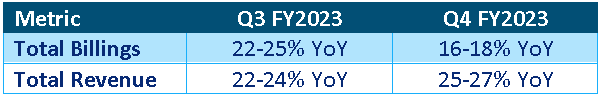
Table 2: Palo Alto FY2023 Guidance (source: Created by author using data from Palo Alto Networks)
Palo Alto has over 60,000 firewall customers and around 10,000 customers across its NGS portfolio, meaning there is still a large opportunity to sell NGS solutions to the existing firewall customer base. Palo Alto believes that vendor consolidation is a large part of its value proposition, and is currently driving growth. This can be seen from growth in the number and value of large deals, which far outpace Palo Alto's total growth. Palo Alto's average deal size is extremely large, and the company is starting to land deals that are truly enormous. For example, Palo Alto did a 75 million USD deal in the second quarter, which was its largest deal ever.
Within XDR, Palo Alto is not targeting the low-end of the market. There are 10,000-15,000 larger organizations that Palo Alto believes could adopt XSIAM in the future, and these are the target.
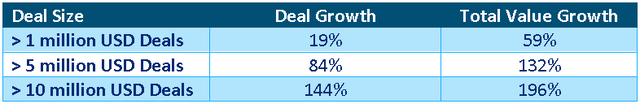
Table 3: Palo Alto Large Deal Growth (source: Created by author using data from Palo Alto Networks)
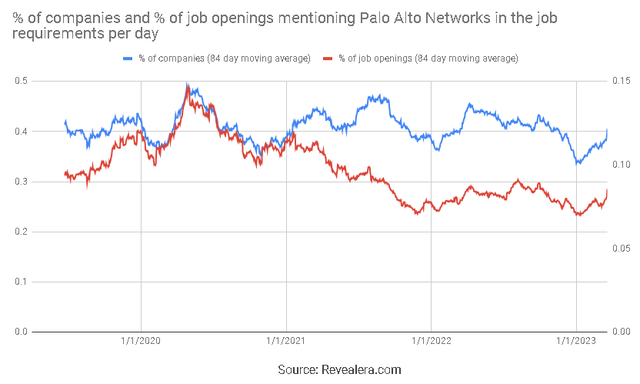
Figure 4: Job Openings Mentioning Palo Alto Networks in the Job Requirements (source: Revealera.com)
The firewall business has seen a surge in recent years, but after demand normalizes and backlogs are worked through, an extended period of weakness is likely. Palo Alto's CEO appears to have become less bullish on hardware in recent months, reducing long-term growth expectations from 5-8% annually, to low to mid single digits.
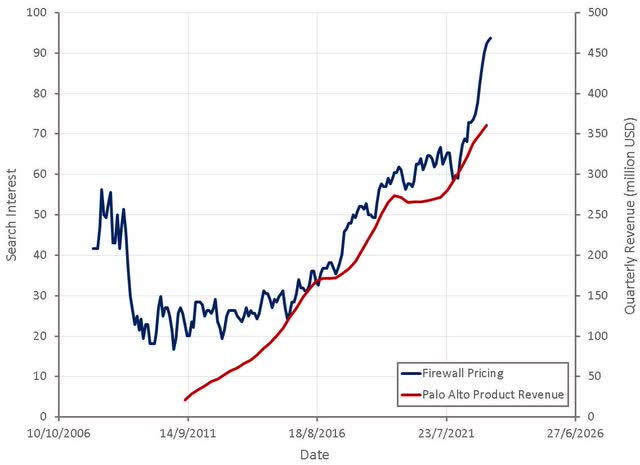
Figure 5: "Firewall Pricing" Search Interest (source: Created by author using data from Palo Alto Networks and Google Trends)
Palo Alto's product gross margins improved significantly in the most recent quarter, due to reduced supply chain challenges. Management has stated that there are lingering effects though, which are expected to dissipate through the rest of 2023. This, along with a growing NGS business, should be supportive of gross margins going forward.
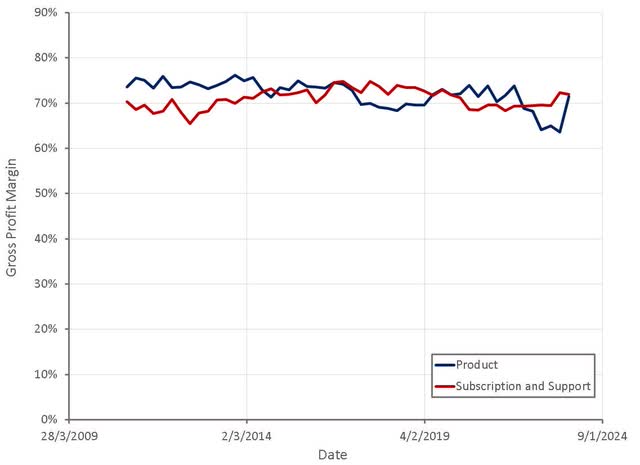
Figure 6: Palo Alto Gross Profit Margins (source: Created by author using data from Palo Alto Networks)
Operating profit margins are also improving, as Palo Alto has reduced investments and is focused on profitability. Palo Alto should start to generate reasonable GAAP margins over the next few years, which is likely part of the reason that the stock has come into vogue with investors.
Palo Alto's scale and broad portfolio of solutions should be supportive of margins, which is something that management has suggested is part of their strategy. If customers adopt multiple solutions, customer acquisition costs are spread across multiple revenue sources.
It is questionable whether this applies to R&D as well though. Management has suggested that because their R&D budget is significantly larger than peers, they have a competitive advantage. R&D investments are spread across a range of products though, rather than being concentrated in a particular area. Unless there are R&D synergies between products, there is unlikely to be a cost advantage maintaining a broad portfolio of solutions.
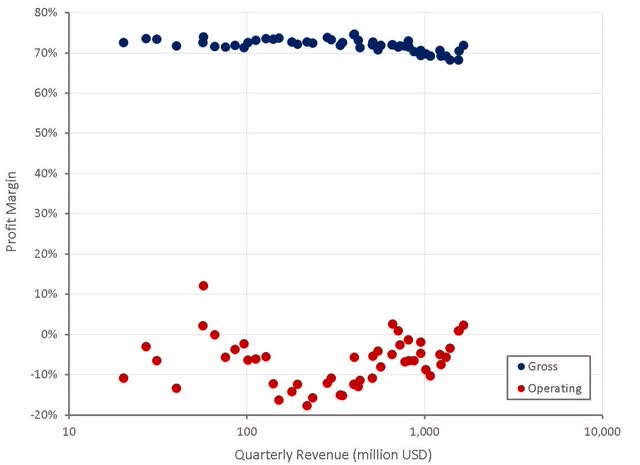
Figure 7: Palo Alto Profit Margins (source: Created by author using data from Palo Alto Networks)
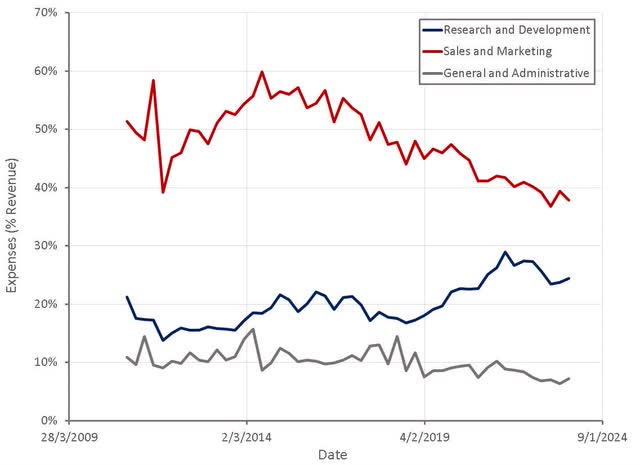
Figure 8: Palo Alto Operating Expenses (source: Created by author using data from Palo Alto Networks)
Palo Alto expects that headcount growth in 2023 will be lower than any of the past three years. This is apparent from job opening data, although the implications are unclear. Less hiring will support margin expansion but could also indicate soft end-market demand.
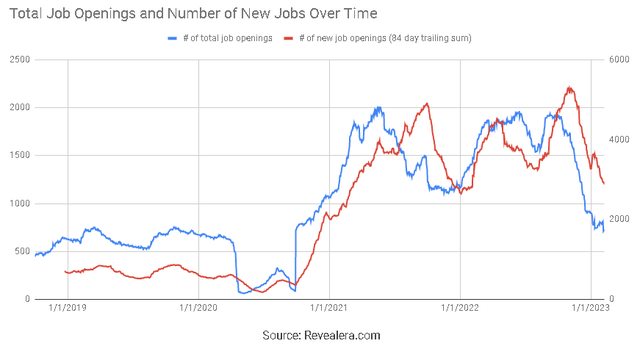
Figure 9: Palo Alto Job Openings (source: Revealera.com)
Valuation
Palo Alto's valuation is quite high given the company's margin and growth prospects. This is likely a result of the company maintaining growth at scale and achieving GAAP profitability, making the stock palatable for a wider range of investors.
Palo Alto has been repurchasing stock, which could be interpreted as an indication that management believes the stock is undervalued. During the second quarter Palo Alto repurchased approximately 1.8 million shares at an average price of around 139 USD per share.
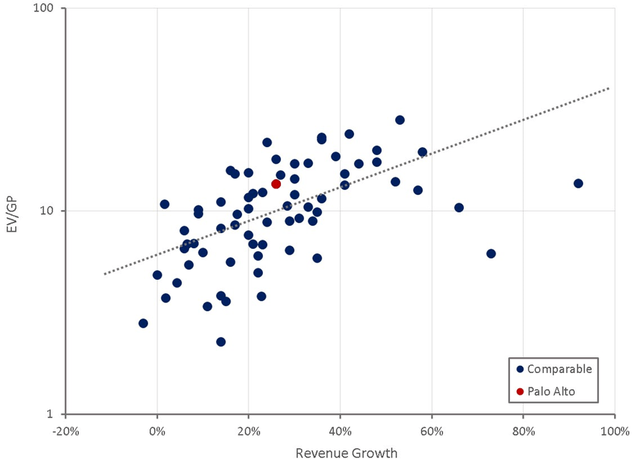
Figure 10: Palo Alto Relative Valuation (source: Created by author using data from Seeking Alpha)
This article was written by
Disclosure: I/we have a beneficial long position in the shares of CRWD, S, NET, SNOW either through stock ownership, options, or other derivatives. I wrote this article myself, and it expresses my own opinions. I am not receiving compensation for it (other than from Seeking Alpha). I have no business relationship with any company whose stock is mentioned in this article.
