 Since its discovery in 2016, the malware has been modified with capabilities to move laterally within affected networks using various exploits, propagate copies of itself, drop other malware into systems, and scout for documents and media files on infected machines. (FILE PHOTO)
Since its discovery in 2016, the malware has been modified with capabilities to move laterally within affected networks using various exploits, propagate copies of itself, drop other malware into systems, and scout for documents and media files on infected machines. (FILE PHOTO) Trickbot, a banking Trojan virus that targets businesses and consumers for their data, has infected over 140,000 devices belonging to customers of Amazon, Microsoft, Google and 57 other corporations since November 2020, according to cyber threat intelligence firm Check Point Research (CPR).
“Trickbot’s numbers have been staggering. We’ve documented over 140,000 machines targeting the customers of some of the biggest and most reputable companies in the world. We went on to observe that the Trickbot authors have the skills to approach malware development from a very low-level and pay attention to small details,” Alexander Chailytko, cyber security research and innovation manager at Check Point Software Technologies, said in a press statement.
CPR observed that Trickbot’s authors are selectively going after high-profile targets to steal and compromise their sensitive data. “At the same time, we know that the operators behind the infrastructure are very experienced with malware development on a high level as well,” he added.
Trickbot is generally used to steal banking information, account credentials, personally identifiable information, and even cryptocurrency. It is a highly modular malware that can be adapted to different use cases, which is what makes it so much more dangerous.
Its infrastructure can be utilised by other malware families to cause more damage. Since Trickbot authors are taking advantage of anti-analysis and anti-deobfuscation techniques allowing the malware to persist on machines, CPR recommends only opening documents from trusted sources.
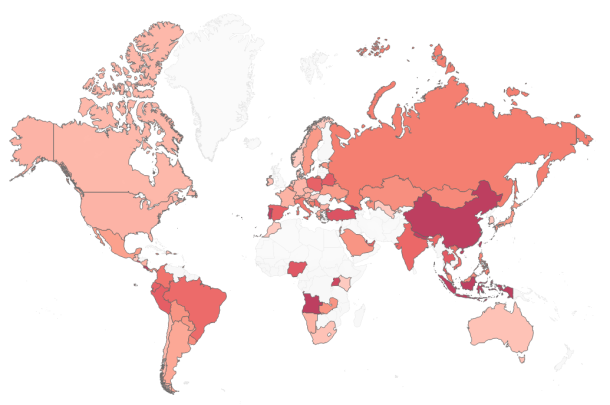 Percentage of organisations’ customers impacted by Trickbot in different regions. The darker the colour, the higher the impact. (Image credit: Counter Point Research)
Percentage of organisations’ customers impacted by Trickbot in different regions. The darker the colour, the higher the impact. (Image credit: Counter Point Research) Some of the other companies whose customers were targeted by the attackers include PayPal, Wells Fargo, American Express, and the Bank of America. In CPR’s list of 60 companies whose customers have been infected by Trickbot, the most infected regions are in the following order: APAC, Latin America, Europe, Africa, North America.
A Trickbot attack typically begins with the attackers sending malicious documents to email addresses. Once the user downloads and opens these documents, the first stage of the malware is executed and the main Trickbot payload is downloaded. The payload is then executed and it establishes its persistence on the infected machine.
Attackers can include modules for spreading through compromised corporate networks, stealing corporate credentials, stealing login details to banking sites etc, as well, according to Check Point.
- The Indian Express website has been rated GREEN for its credibility and trustworthiness by Newsguard, a global service that rates news sources for their journalistic standards.

