insider threat
An insider threat is a category of risk posed by those who have access to an organization's physical or digital assets.
These insiders can be current employees, former employees, contractors, vendors or business partners who all have -- or had -- legitimate access to an organization's network and computer systems.
The consequences of a successful insider threat can take a variety of forms, including a data breach, fraud, theft of trade secrets or intellectual property, and sabotage of security measures.
What are the different types of insider threats?
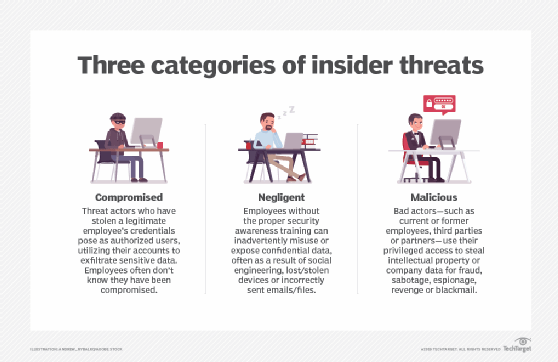
Insider threats are defined by the role of the person who introduces the threat. The following are several examples of potential insider threats:
- Current employees could use privileged access to steal sensitive or valuable data for personal financial gain.
- Former employees could retain access to an organization's systems or pose a security threat by sabotaging cybersecurity measures or stealing sensitive data as a means of payback or personal gain.
- Moles are external threat actors who gain the confidence of a current employee to get insider access to systems and data. Often, they're from an outside organization hoping to steal trade secrets.
- Unintentional insider threats aren't caused by malicious employees, but rather, insiders who inadvertently pose a significant risk because they don't comply with corporate security policies or use company systems or data in a negligent manner. While unintentional, reckless behavior can open the door to external threats, like phishing, malware or endpoint
Why are insider threats dangerous?
Insider threats can be hard to detect, even using advanced security threat detection tools. This is likely due to the fact that an insider threat typically doesn't reveal itself until the moment of attack.
Furthermore, because the malicious actor looks like a legitimate user, it can be difficult to distinguish between normal behavior and suspicious activity in the days, weeks and months leading up to an attack. With authenticated access to sensitive data, the insider exploit might not be apparent until the data is gone.
With few safeguards preventing someone with legitimate access from absconding with valuable information, this type of data breach can be one of the most costly to endure.
"Cost of a Data Breach Report 2020," a study produced by Ponemon Institute with IBM Security sponsorship, noted that "the average cost per lost or stolen record was $146 across all data breaches," but the cost went up to $150 for records containing customer personally identifiable information. The report also noted that 19% of companies experienced a malicious data breach because they were "infiltrated due to stolen or compromised credentials."
What are the warning signs that could indicate an insider threat?
To build awareness and improve detection of insider threats, there are several common signs that could indicate the presence of inappropriate insider activity in your organization:
- disgruntled employee behavior, such as displays of anger, exhibiting a negative attitude or talking about quitting;
- evidence of a user trying to circumvent access controls;
- dismantling, turning off or neglecting security controls, such as encryption or maintenance patches;
- frequently working late or in the office during off-hours when few others are present;
- violation of other corporate policies that may not be related to computer use;
- accessing or downloading large amounts of data;
- accessing -- or attempting to access -- data or applications that are not associated with an individual's role or responsibilities;
- connecting outside technology or personal devices to organizational systems or attempting to transmit data outside the organization; and
- searching and scanning for security vulnerabilities.
How can you defend against insider threats?
The Ponemon/IBM Security report identified several areas where modern organizations may be exposing themselves to insider threat incidents.
A lack of a baseline on nonmalicious, routine user behavior as a means of comparative analysis against suspicious behaviors was noted as a key shortcoming.
Another potential vulnerability resulted from poor identity management and access control protocols. An abundance of privileged accounts is an ideal target for social engineering and brute-force attacks, such as phishing.
To fill these gaps, there are two main paths forward: building awareness through proper training and using prevention and detection security measures.
Awareness and training program implementation
Employees should be properly trained on security risks so that they understand how to use the organization's systems safely and securely.
Security teams should specifically be trained on insider threat detection. Doing so can help them to better spot suspicious activity and prevent data loss or damage from insider attacks before they occur.
Detection and prevention security measures
In addition to improving employee training and awareness, most organizations have begun implementing insider threat programs that incorporate insider threat mitigation through detection, as well as prevention. This can be accomplished through compliance, security best practices and continuous monitoring.
Many cybersecurity tools can scan and monitor functionality to discover threats such as spyware, viruses and malware, as well as provide user behavior analytics.
Security controls can also be implemented to protect your data sources. Examples include encryption for data at rest, routine backups, scheduled maintenance and enforced two-factor authentication for password fortification.
Furthermore, identity management tools often automate user access revocation when an employee is terminated. These tools also provide greater control over what your employees have access to, so access to sensitive data sources can be limited.
How to get started with insider threat detection and prevention
Protect your sensitive data and systems
There are several methods that can help you to better protect your company's data and critical systems. Investing in data loss prevention tools is one option, but you should also consider data classification, vendor management, and other risk management and security policies that can better prevent data breaches.
Implement behavioral analytics and employee tracking
As noted earlier, insider threats can be difficult to uncover using manual processes alone. Sophisticated tracking tools, like user and entity behavior analytics, use artificial intelligence to detect even minimal changes in patterns that humans may not see.
Reduce the attack surface through continuous monitoring
Continuous monitoring tools and attack surface management (ASM) help by constantly scanning computing systems and networks, taking an inventory of vulnerabilities, prioritizing them and sending user alerts when action is required.
Patch vulnerabilities
As new vulnerabilities are found, either through continuous monitoring, ASM tools or vendor notifications, be sure to patch them right away. The holes in your defenses are the perfect opportunity for external threats to gain a foothold in your ecosystem.
For additional detail on preventing insider threats, read "10 ways to prevent computer security threats from insiders."






