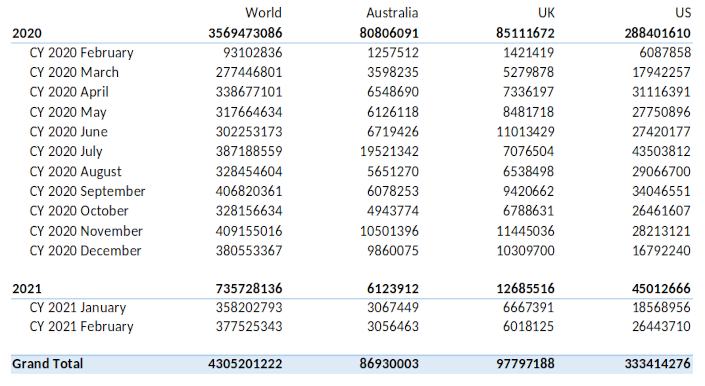
The company said in a statement that the numbers in the UK for the same period were 97.7 million, while for the US it stood at 333.4 million.
RDP is a proprietary protocol developed by Microsoft and it has a graphical interface for connecting to another computer over a network connection. The user has to run the RDP client while the target computer must be running RDP server software.

The Kaspersky statement tied the number of attacks to the fact that the WHO declared a pandemic in mid-March and a good portion of the globe's workforce began working from home.
"One of the most common was attacks against the protocols used by employees to access corporate resources remotely."

After the switch to remote work, the number of brute-force attacks using RDP skyrocketed, Kaspersky found.
"According to Kaspersky’s telemetry, when the world went into lockdown in March 2020, the total number of brute-force attacks against RDP jumped from 93.1 million worldwide in February 2020 to 277.4 million in March — a 197% increase," the company said.
"From April 2020 onward, monthly attacks never dipped below 300 million, and they reached a high of 409 million attacks worldwide in November. In February 2021 — nearly one year from the start of the pandemic — there were 377.5 million brute-force attacks – a far cry from the 93.1 million witnessed at the beginning of 2020."
In Australia, July 2020 saw a significant spike to 19.52 million attacks. The holiday season also witnessed high numbers, with November at 10.5 million and December at 9.8 million, while other months averaged between three to seven million.
“Remote work isn’t going anywhere. Even as companies begin considering re-opening their workplaces, many have stated that they will continue to include remote work in their operating model or pursue a hybrid format," said Kaspersky security expert Dmitry Galov.
"That means it’s likely these types of attacks against remote desktop protocols will continue to occur at a rather high rate. 2020 made it clear that companies need to update their security infrastructure, and a good place to start is providing stronger protection for their RDP access."
