Minerva Studio - Fotolia
Comparing inbound and outbound firewall rules for the enterprise
Explore the differing roles of inbound versus outbound firewall rules for enterprise network security and the varying use cases for each.
It is vital to compare the roles of inbound and outbound firewall rules before purchasing a corporate firewall in order to ensure quality security for your enterprise's IT environment. Here, I'll explain the differences between the two, as well as the benefits and drawbacks of each.
Inbound traffic vs. outbound traffic
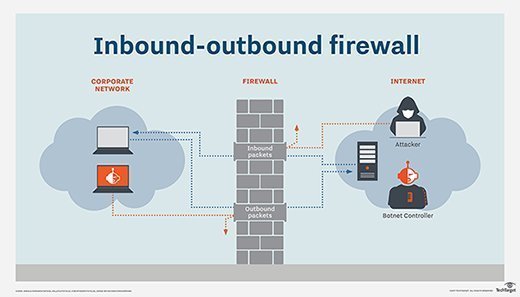
Enterprise networks have both inbound traffic and outbound traffic. The inbound requests originate from outside parties, such as a user with a web browser, an email client, a server or application making service requests, like FTP and SSH, or API calls to web services.
Outbound requests, on the other hand, originate from inside the network, destined to services on the internet or outside network. Firewalls are typically designed to prevent inbound traffic from entering a network, but their use can also prevent outside connections from outbound traffic.
The difference between inbound and outbound firewall rules
Simply put, inbound firewall rules protect the network against incoming traffic from the internet or other network segments -- namely, disallowed connections, malware and denial-of-service (DoS) attacks. Outbound firewall rules protect against outgoing traffic, such as requests to questionable or dangerous websites, VPN connections and email services, such as Post Office Protocol version 3, Internet Message Access Protocol and Simple Mail Transfer Protocol. A single firewall typically serves both functions.
The configuration of such firewalls is business-, network- and risk-specific, so the configuration for, say, a manufacturing business's firewall will likely be a lot different than that of a cloud service provider's firewall. Customizable firewall rules allow specific ports, services and IP addresses to connect in or out.
Sometimes, a dedicated firewall appliance or an off-site cloud service, such as a secure web gateway, is used for outbound traffic because of the specialized filtering technologies necessary. Such systems often perform targeted functions, like content filtering for email or web browsing. They often tie into the business's directory service -- Active Directory and Lightweight Directory Access Protocol -- so they can provide access, filtering and reporting based on each user's network account. Other firewall systems look for outbound malware and security-related threats, including DNS lookups to hosts that are known to be threatening or even blacklisted.
Using outbound firewall rules
While managing outbound traffic introduces a certain level of complexity into the environment, it is still becoming a popular approach to network security. Often, outbound firewalls interrupt application traffic, disrupt business workflows and upset users unless admins pay close attention to configuring the firewall in a way to that enables rather than hinders work.
However, in certain cases, businesses might need to filter outbound traffic. For example, outbound firewall rules can be beneficial in locked-down environments that control network behavior down to the host, application and protocol levels. Alternately, certain data loss prevention technologies may need outbound firewall rules to protect specific information on the host.
Analyzing and controlling outbound traffic has become more important today as security teams look to prevent the exfiltration of sensitive data or other malicious activity involving malware and DoS attacks from insider threats.
Using inbound firewall rules
Most organizations have been using inbound firewall protection for years. Inbound firewall rules serve to protect internal network systems from outside threats. They can be located at the network perimeter, branch office locations or even internally, providing further network segmentation and protection. Inbound firewall rules meet the goal of keeping bad things out and safe things intact.
Inbound and outbound firewall rules require not only system configuration, but also monitoring for system anomalies. Even the most secure firewalls can only do so much. Without the necessary internal resources -- product training, security knowledge and so forth -- for managing your firewall environment, a great option is to outsource to a managed security service provider (MSSP). Having a dedicated resource like an MSSP monitoring network security around the clock is often the best way to minimize the associated risks.









