 The ‘Sign in with Apple’ works similarly to OAuth 2.0. (Image: Bhavuk Jain/27year-old Indian developer)
The ‘Sign in with Apple’ works similarly to OAuth 2.0. (Image: Bhavuk Jain/27year-old Indian developer)
Apple has reportedly paid $100,000 (around Rs 75 lakh) to an Indian developer for finding a critical bug in the ‘Sign in with Apple’ process. Bhavuk Jain, a 27-year-old developer discovered a “Zero Day” bug in the ‘Sign in with Apple’ process that could have allowed hackers to take over user’s account on the third-party application.
“What if I say, your Email ID is all I need to take over your account on your favourite website or an app. Sounds scary, right? This is what a bug in ‘Sign in with Apple’ allowed me to do.” Jain said in a blog post.
“In the month of April, I found a zero-day in ‘Sign in with Apple’ that affected third-party applications which were using it and didn’t implement their own additional security measures. This bug could have resulted in a full account takeover of user accounts on that third party application irrespective of a victim having a valid Apple ID or not,” he added.
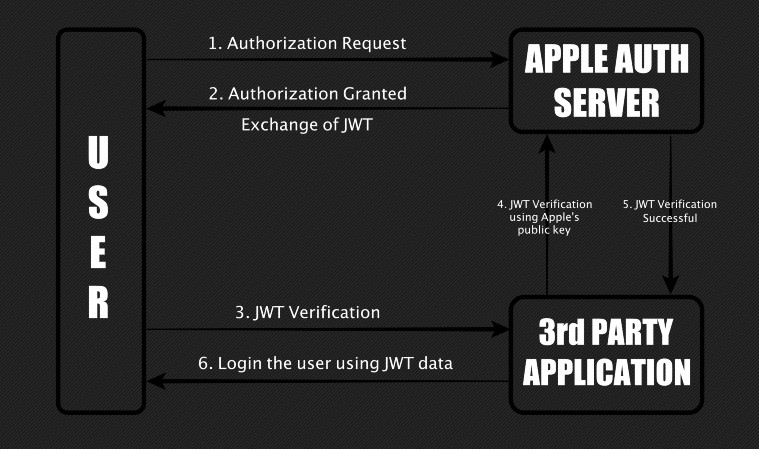 How the Sign in with Apple process works. (Image: Bhavuk Jain)
How the Sign in with Apple process works. (Image: Bhavuk Jain)
‘Sign in with Apple’ was introduced in June last year. It allows users to set up a user account to sign in to third party apps with their Apple ID without having to use their email address. This is done by generating a JSON Web Token or JWT, which contains the information required by the third-party application to confirm the identity of the user while preserving user privacy. However, the Zero Day bug exposed the user accounts to attacks.
Jain explained in his blog post that there was no validation to check if the same user who generated the JWT is requesting the JWT to login to the third-party account. Hackers could have exploited the vulnerability by faking a JWT. Since a lot of developers have integrated ‘Sign in with Apple’, this vulnerability could have proved quite critical.
In his blog post, Jain also said that he was paid 100,000 by Apple under their Apple Security bounty program for discovering this vulnerability. The issue has been resolved. Jain added that Apple did an investigation of their logs to determine there was no misuse or account compromised due to this vulnerability.
