Passwords are an integral component of security hygiene, but beyond password strength requirements, it’s largely a user-driven initiative. The Digital Guardian surveyed 1,000 internet users to gain some insight into current password habits, how frequently users implement best practices for password hygiene, what methods users rely on to remember the abundance of passwords they manage, and other details that shed some light on the current state of password hygiene.
Check out the infographic below for a summary of our findings and read on for more analysis.
Infographic by Digital Guardian
About the survey
The Digital Guardian surveyed a randomly selected group of 1,000 Google users in the United States, from ages 18 and up. The survey included seven questions:
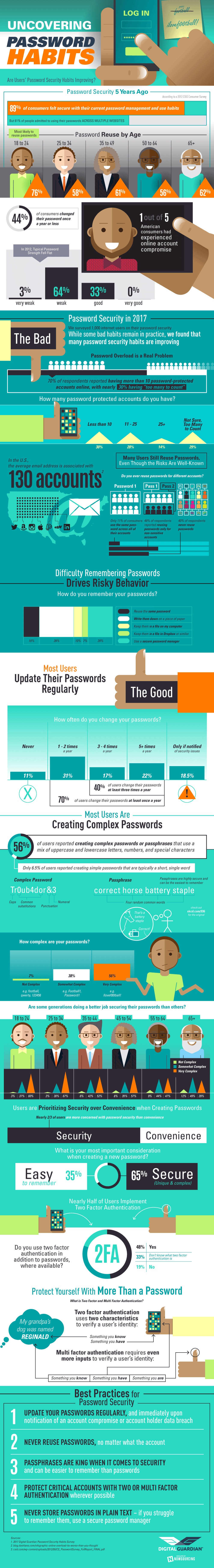
- How many accounts do you have that require a password?
- How often do you change your passwords?
- Do you ever reuse passwords for different accounts?
- How complex are your passwords?
- What is your most important consideration when creating a new password?
- Do you use two-factor authentication in addition to passwords, where available?
- How do you remember your passwords?
Password overload is real
Previous data from companies like Dashlane has found that people generally have far too many passwords to remember. In fact, a Dashlane analysis of data from more than 20,000 users in 2015 found that the average user has 90 online accounts. Delving further into the data sample, Dashlane found that in the US, there are an average of 130 accounts assigned to a single email address.
The survey results indicate that password overload is still a very real concern for many users, although there’s an interesting split between the number of people who have far too many passwords to remember and those who manage less than 10 accounts that require passwords.
Among 999 responses to this question:
- 29% of respondents aren’t even sure how many accounts they have requiring a password; there are simply too many to count.
- 29.7% of respondents indicate that they have less than 10 accounts requiring a password.
- 13.6% say they have more than 25 accounts that require a password.
- 27.6% report having between 11 and 25 accounts requiring a password.
Most users updates their passwords frequently
There’s a lot of information out there surrounding the recommended frequency of password changes along with debate around how often is too often when it comes to mandatory password changes. Recent information suggests that too-frequent mandatory password changes could actually have an adverse impact on security. According to Lorrie Cranor, Chief Technologist at the Federal Trade Commission, people who are required to change their passwords too frequently are more likely to choose less-secure passwords to begin with. When it’s time to make a mandatory change, these same users tend to make subtle changes that are easily predictable by attackers rather than create entirely new, strong passwords. But how frequent is too frequent, and how often does the average user change their own passwords?
The survey results indicate that nearly one-third (31.3%) of respondents change their passwords one to two times per year. Just over one-fifth (22.4%) change their passwords more than five times per year, and 17% change their passwords every few months, or approximately three to four times per year. As long as the latter groups (the nearly 40% of users that reported changing passwords 3 or more times per year) are comfortable with the frequency of their changes and are practicing sound password security habits such as creating complex passwords, avoiding password reuse, and using secure password management practices, we should take this as a positive sign.
Overall, 29.4% of respondents change their passwords rarely or never:
- 10.9% of respondents say they never change their passwords.
- 18.5% change their passwords only when they’ve been notified of a security issue.
About half of respondents reuse passwords, but not always
Most security experts recommend that you maintain unique passwords for all of your accounts, never reusing passwords across profiles or accounts. Why? Simple: If an attacker discovers your password to one account and it happens to be the same password you use on every account, you’ve just given them access to your entire digital life. Some experts say that password reuse is the biggest problem in security today.
Most people realise it’s a bad idea to use the same password across multiple accounts, yet some continue to do it anyway. In our survey, among the 941 responses to this question:
- 49.3% say they do reuse passwords sometimes, but only for unimportant or non-critical accounts.
- 39.9% say they never reuse passwords (promising!).
- 10.8% have only one default password that they use across most or all accounts (bad news).
Users are savvy about password complexity
It’s fairly widely known that simple, easy-to-guess passwords are insecure. Your dog’s name, your spouse’s name, your birthdate, and other words and phrases related to your life that are easily discoverable on your social media profiles are just that – easy for attackers to discover. An increasing number of accounts require certain elements to ensure that passwords achieve a minimum security threshold by adding mandatory complexity. For instance, you’ve probably encountered passwords that require:
- A combination of uppercase and lowercase letters
- Numbers
- Special characters or symbols
- A minimum number of characters
By requiring users to select passwords that include all (or in some cases, a mix of the four) elements results in passwords that are more difficult to crack, enhancing account security for users.
There’s some debate within the IT security community regarding whether password complexity or length is more critical to security. Lengthy passwords have exponentially more possible random character combinations and thus take longer for password-cracking tools to crack. A combination of complexity and length is logically the best way to go about creating strong passwords.
According to the survey results, users are embracing the value of password complexity. Among the 884 responses to this question:
- 55.8% use very complex passwords/passphrases, such as “Ilovef00tball!”.
- 37.8% use somewhat complex passwords, such as “Football1”.
- Only 6.5% rely on passwords that are not at all complex, such as common words or phrases like “football,” “qwerty,” or the tried-and-failed pets’, children’s, or spouses’ names.
The most important password considerations
As users are becoming savvier about best practices for password security, what are they prioritizing when creating strong passwords? With so many accounts to manage and passwords to remember, it’s no surprise that creating easy-to-remember passwords remains a priority for many users and competes with the need for strong, complex passwords to enhance security.
According to our survey results, 65.3% of the 869 responders to this question say that their most important consideration is security, focusing on creating passwords that are both unique and complex. On the other hand, more than one-third (34.7%) place greater importance on having passwords that are easy to remember.
However, the two are not mutually exclusive. Techvera provides some tips for creating passwords that are both secure and easy to remember, such as using passphrases rather than passwords, using strings of random words in a nonsensical order, or by using random password generators in combination with password managers (to alleviate the need to remember dozens of unique, complex passwords). Additionally, UberGizmo offers some solid advice for creating strong yet easy-to-remember passwords, explaining that while passphrases are powerful memory tools, you should use a unique approach to create a passphrase that’s easy for you to remember, but incredibly difficult for anyone other than you to guess.
The use of two-factor authentication
Security experts always recommend using two-factor authentication where possible, providing an added layer of security and a roadblock for would-be attackers attempting to crack your password. Again, this is a best practice that more users are aware of today, yet it’s not readily embraced by the majority. Some people consider two-factor authentication to be time-consuming and frustrating, adding another layer of verification for their own use of their accounts.
In the survey, 840 participants responded to this question. The results are a mixed bag; more than twice as many people say they use two-factor authentication where it’s available (47.8%) compared to those who don’t (19.4%). That said, a surprising 32.8% of respondents say they don’t know what two-factor authentication is.
Essentially, two-factor authentication involves two distinct steps (or factors) to verify a user’s identity; typically some combination of the following:
- Something you know (e.g., your password or your username)
- Something you have (e.g., your ATM card, mobile phone, or an access token/badge)
- Something you are (typically verified with biometrics, such as iris scans, fingerprints, or facial recognition)
Think about the ATM example and you’ll realise just how common two-factor authentication really is. Two-factor authentication is inherently more secure; while it may be easy for a attacker to crack your password, replicating your fingerprint or obtaining your physical property can be a much harder feat. While biometrics are less commonly used than other methods of authentication due to technology limitations, the use of biometrics is starting to grow as well. A 2016 survey by TeleSign found that more than half of companies surveyed (54%) had plans to implement biometrics as a security measure.
Password recall: How users remember their passwords
With the average person maintaining 90 or more accounts that require passwords, many of which require more complex and lengthier passwords to bolster security, people are forced to find a way to remember all those passwords.
In the survey, 800 respondents answered this question. The Digital Guardian found that people are using a number of different tactics in an effort to recall their passwords, including:
- 38.6% write their passwords down on a piece of paper.
- 27.7% use a secure password manager.
- 17.7% reuse the same password for multiple accounts.
- 9.5% keep all their passwords in a file on their computer.
- 6.6% store their passwords in a file in Dropbox or a similar storage repository.
Kaspersky examined this same question in a 2016 survey of more than 12,500 people from 21 countries, with slightly different findings:
- 53% of respondents reported remembering their passwords.
- 22% of respondents reported writing their passwords down in a notepad.
- 11% write passwords on a piece of paper or sticky note that they keep near their computer.
- 11% store their passwords in their web browser.
- 10% document passwords in a file stored on their computer.
- 9% store passwords in their smartphone.
- 7% store their passwords in a specialized software application.
- 6% send themselves an email with their passwords.
- 4% store their passwords in an online service.
- 4% use some other method not described above.
- 7% responded “don’t know.”
PasswordResearch.com also has some data about the ways people remember their passwords, with the results similarly dispersed across tactics. It’s clear that people rely on a multitude of tactics to remember their passwords for the many digital services they access.
So what’s the best way to keep track of all those passwords? According to Brain Krebs of Krebs on Security, “The most secure method for remembering your passwords is to create a list of every Web site for which you have a password and next to each one write your login name and a clue that has meaning only for you. If you forget your password, most Web sites will email it to you (assuming you can remember which email address you signed up with).”
Krebs admits that his view on keeping a written list of passwords has evolved over time, and with the ever-changing security landscape, it’s a safe bet to assume that’s the case for many experts as attackers become increasingly sophisticated. If you do store your passwords in a central list or file, avoid storing them in plain sight or in plain text, suggests Krebs. Apps that manage passwords can be useful, he says, and there are local applications that aren’t stored in the cloud. The key is to create a robust primary password that you won’t forget; if you do forget it, you’re probably out of luck.
More education on password hygiene is needed
So what’s the key takeaway from these findings? While some results are promising, indicating that people’s knowledge of the need for strong, secure passwords is growing, far too many users continue to rely on outdated and insecure password practices that place their security at risk. Some may not realize how risky their password behaviors are, while others simply opt for the easier route knowing that they’re sacrificing some security for the sake of convenience.
It may seem like a minor issue when it comes to accounts that contain little to no sensitive, personal information, but if you’re reusing the same password across multiple accounts, cracking one of those less-important accounts opens the gates to your digital life. If you’re not yet using robust password practices, it’s time to step up your game.
Published from permission. This article first appeared on Digital Guardian
Published from permission. This article first appeared on Digital Guardian